Office 365 some time crashes if "Block signing into Office" policy is enabled. To resolve this application crash, you need to disable this policy. You can control the policy settings via the Windows Registry Editor.
Today we will learn about this policy settings and how to block signing into Office by modifying the Windows Registry value.

If you encounter crash in Microsoft Office applications with the fault module name as mso20win32client.dll, this might be because the "Block signing into Office" policy is enabled for your Office 365 installation and set as "None Allowed".
This blocks user to sign in to Office 365 services using Microsoft Account and Organization Account. Here is the error log that you see from Event Viewer:
Faulting application name: [APPLICATION].EXE, version: 16.0.10228.20080, time stamp: 0x5b4dd3c9
Faulting module name: mso20win32client.dll, version: 0.0.0.0, time stamp: 0x5b2989f4
Exception code: 0xc0000005
Fault offset: 0x0000000000031cd0
Faulting process id: 0x1f34
Faulting application start time: 0x01d390e8c20433d4
Faulting application path: C:\Program Files\Microsoft Office\root\Office16\[APPLICATION].EXE
Faulting module path: C:\Program Files\Common Files\Microsoft Shared\Office16\mso20win32client.dll
Report Id: 4b6c6d7d-fd1b-11e7-9203-448a5be655b6
To resolve this error causing the crash in Office applications, you need to block signing into Office by modifying a registry value. Follow the steps mentioned below to modify the policy settings. Make sure that, you have administrative rights in order to open/modify registry data.
Warning:
Using Registry Editor incorrectly can cause serious, system-wide problems that may require you to re-install Windows to correct them. Neither the owner of this post, the site and Microsoft guarantee that any problems resulting from the use of Registry Editor can be solved. Use this tool at your own risk.
Open your Windows Registry Editor (regedit) and navigate to the following registry path: HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\Internet. Here you will find a DWORD policy settings named UseOnlineContent.
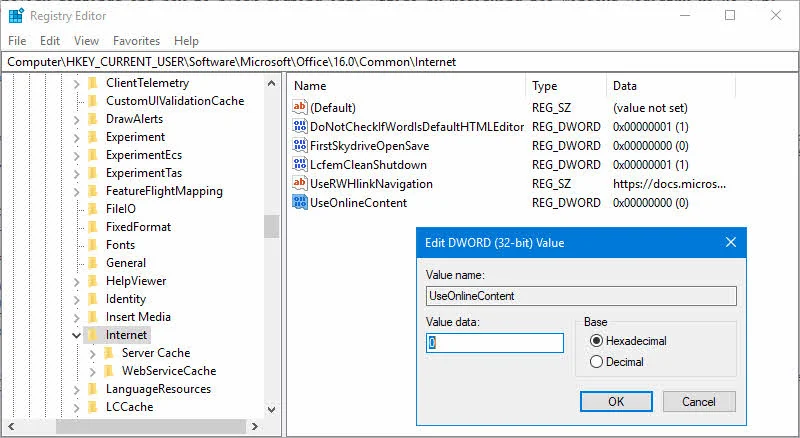
This allows you to enable/disable the signing into Office and control whether users can provide credentials to Office using their Microsoft Account (MSA) or the User ID provided by their organization to access Office 365 services.
It can have 4 different values:
- 0 - When you set it as DWORD value '0' (both IDs allowed), it allows users to sign in to Office 365 services by using Microsoft Account or Organization Account.
- 1 - When you set it as DWORD value '1' (Microsoft account only), it will allow users to sign in to Office 365 services using Microsoft Account only.
- 2 - When you set it as DWORD value '2' (Organization account only), it will allow users to sign in to Office 365 services using users Organization Account only.
- 3 - When you set it as DWORD value '3' (none allowed), the user cannot sign in to Office 365 services. None of the Microsoft Account and Organization Account will work.